Authors: Subodh Kumar, Vijay Anant Athavale & Divye Kartikey
Abstract
In recent years, cloud computing has developed into one of the fastest growing areas in the IT industry and a key driver for achieving an organization’s mission. Some examples of cloud computing are: Google apps, data centre services, infrastructure, software, virtualization and platform-as-a-service. Microsoft, HPE, IBM, Amazon Web Services, Google, SalesForce, NetSuite, and VMware are some of the leading cloud computing companies. Despite the numerous benefits of cloud computing, it presents many unique security issues and challenges due to which companies are concerned about the security of their data once it leaves the firewall. Nowadays, security is a top concern for IT professionals worldwide and want to ensure their cloud data to be prevented from being leaked, stolen or deleted. This article seeks to present a comprehensive picture of cloud computing security, as well as identify and analyse the most vulnerable security concerns and cloud computing threats, so that end users and service providers are aware of the important security concerns and threats associated with cloud computing.
Keywords: Cloud Computing, Security issues, Data breach, Personal information, Cyber attack
Introduction
Cloud computing is the on demand availability of technology enabled services to the people and organisations by allowing convenient network access to a shared pool of configurable computing resources like: storage, networks, servers, applications, and services over the internet, from anywhere, at any time, from data centres around the world. Some examples of cloud services are Microsoft, HPE, IBM, Amazon Web Services, Google, SalesForce, NetSuite and VMware.
The overcapacity of today’s huge corporate data centres, the accessibility of broadband and wireless networking, the dropping cost of storage, and continuous advancements in networking technology are all driving forces behind the rise of cloud computing.
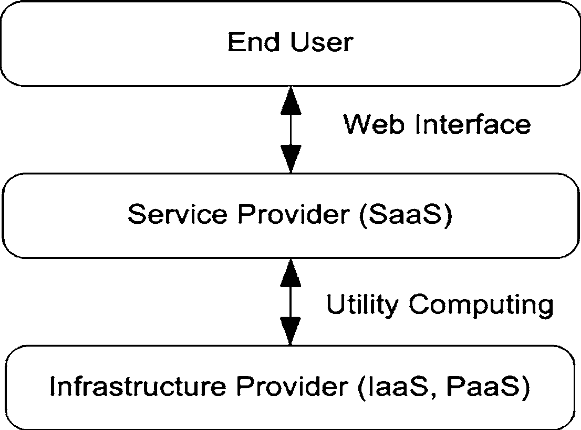
Cloud computing is growing rapidly as a means of renting computing and storage infrastructure services (known as IaaS or Infrastructure as a Service), building and personalising remote platforms for business processes (known as PaaS or Platform as a Service), and renting entire business applications (known as SaaS or Software as a Service). The cloud infrastructure is further classified as Public, Private and Hybrid Cloud.
Latest numbers show that the cloud is providing organizations with a 21% reduction in product time to market, a 17% reduction in IT maintenance costs, a 15% reduction in IT spend, and an 18% increase in employee productivity. With these types of metrics in hand it’s no surprise that 60% of CIOs state that the cloud has become their 1st priority [1].
According to a recent research by the Cloud Security Alliance (CSA), the development in cloud computing has introduced many security concerns, and the security of data in the cloud is now a broad-level issue for 61 percent of enterprises. 77 percent of respondents of a survey conducted in 2018 have stated that the cloud computing security risk has become a major concern.
Although most business owners believe that the cloud environment is more secure than an on-premise infrastructure, there are still a number of concerns which need to be addressed [2]. A survey of IT executives revealed that some of the top security issues that hold back cloud adoption at their companies include data breach, data loss, insider threats, DoS (Denial of Service), cryptojacking, account hijacking, insecure APIs, disaster recovery and business continuity. In terms of cloud security, password monitoring is crucial. Your cloud account gets less secure the more people that have access to it. The information saved in the cloud will be accessible to anyone who knows your password. As per a research by Skyhigh, an enterprise experiences around twenty three cloud-related threats every month [3].
Two commonly used categories for classifying cloud computing are:
- Service boundary
- Service type
From the perspective of service boundary, cloud computing can be categorized as:
- Public Cloud
- Private Cloud and
- Hybrid Cloud
The service provided to external parties when the infrastructure is completely outside the customer or company’s firewall is called the Public Cloud.
When IT services are placed on top of large scale consolidated and virtualized infrastructure within an enterprise firewall and used on the basis of ‘per transaction’ which the corporations create and operate, it is called Private Cloud.
When theresources are shared between a public and private cloud by a secured network, it is called Hybrid Cloud. Examples of hybrid cloud include Amazon’s VPC (Virtual Private Cloud) services and Google.
From the perspective of service type, cloud computing can be categorized as:
- IaaS (Infrastructure as a Service)
- PaaS (Platform as a Service)
- SaaS (Software as a Service)
SaaS caters to end users, whereas IaaS and PaaS cater to Independent Software Vendors (ISVs) and developers leaving a margin for third-party application developers.
Security Objectives
- To ensure that information is always available.
- To maintain the integrity of information and services.
- To protect the privacy of information stored on participating systems.
- To verify the authenticity of communicating partners.
- To provide control over access to services or their components in order to ensure authorised service use.
- To ensure that origin and delivery of data is not repudiated.
- To ensure that there will be no data leakage after separation of data and processes on the virtual level of cloud between various applications.
- To maintain the same level of security during addition or removal of resources on a physical level.
Research Challenges
Despite the fact that cloud computing has been publicly accepted by the industries, many current concerns remain unresolved, and new challenges continue to emerge from industry applications. Some challenging research concerns in cloud computing include:
- Data security
- Server consolidation
- Software frameworks
- Storage technologies
- Data management
- Traffic management and analysis
- Virtual machine migration
- Automated service provisioning
- Energy management





